The basic requirement you need to have to gathering information is having your Virtual machine ready and install Backtrack, mine is Backtrack 5. Here is what its looks like:
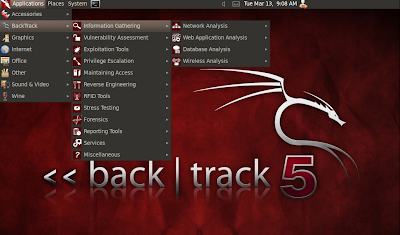 As you can see, there are plenty tools you can use for each step of doing penetration testing. But be patient, we are still learning on the Information Gathering, and let us be structured, shall we?
As you can see, there are plenty tools you can use for each step of doing penetration testing. But be patient, we are still learning on the Information Gathering, and let us be structured, shall we?I will be more focus on using one tool for gathering a website's information, it is called Maltego. Maltego is basically a forensic application. It offer you to mining and gathering information as well as the representation of this information in an easy to understand format since it is using GUI. Especially for us, beginners.
1. Choosing Maltego application
After you choose Network Analysis menu from the previous screen shot, choose DNS Analysis menu on the next menu, then choose Maltego on the bottom of the menu. You must first register in order of using this tools, so make sure that your Virtual Machine is connected to the internet. After the registration is completed, you will now be to play with maltego and it will appear just like this.
2. Determining the target website.
Drag and Drop "DNS Name" from the Infrastructure Palette to the Graph. Double Click the icon, and it will appear a pop up to enter the target website. It will looks like this.
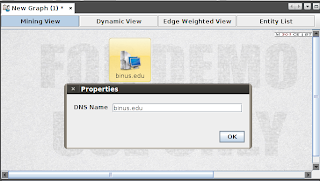
3. Run Transformation
In this step, you will transform a DNS name to Domain, to IP address, or to Website by right clicking the icon and choose Run Transform -> All Transform. The result of each option will be looks like this.
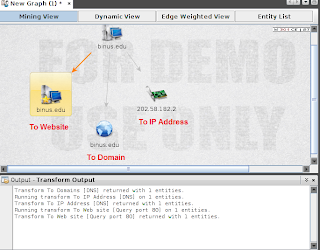
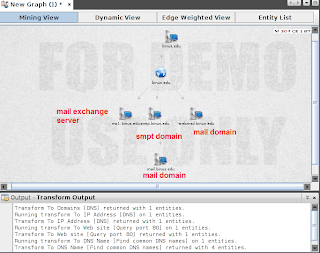
4. Finding Subdomain
You don't really need to use all of the option available to do this.
Now you can get the list of available subdomains in binus (dot) edu. You can also find the mail server domain by right-clicking the Domain of binus(dot)edu, and choose All Transform -> To DNS Name [Find Commons DNS Names]. And it will appear just like this.
5. Finding Email of respective website
You can find any email address available in this domain. This time, I'm using transformation To Email Address [using Search Engine]. And the result will be like this.

Since now you can have the email address available on that domain, now you can even find the person who owns or manage the account. You can find it using the To Person option on the mail icon, and you can even find out whether they have subscribe on filckr or even myspace. You can even find out their telephone number if they have unaware to ever post it down to the Internet and let the search engine from this tool do the work.
IMPORTANT!
You should be aware as an Ethical Hacker this activity is only used for gathering information towards the target so that we can fix the format, or anything that will prevent this tools to finds such information any more of the respective website. You may not do this for stalker purpose, getting on their telephone number and text them "hey, I know who you are and I'm standing outside your door". Kindly bear in mind, that this is closely related with privacy issues. I hope you can do this activity in ethical way.
So fun to share things I just have learnt!
wuih, calon2 CEH..
ReplyDeleteHacker to be, uhuyyy!!
ReplyDelete